
The European cyber security organisation published a new report this week on cyber ranges. The report attempts to help the market understand “Cyber ranges and the associated technologies and use cases” by using a range of criteria “to better evaluate the capabilities of different cyber ranges”.
Cyber ranges are “a new emerging and trendy technology” and have increased in use during the past number of years. Popularity has increased hype and in turn, has led to some confusion over what a cyber range can and cannot do.
Due to the highly customisable ability of cyber ranges there are some various definitions, however the official ECSO definition describes a cyber range as “a platform for the development, delivery and use of interactive simulation environments.” A simulated environment is a representation of an organisation’s ICT, OT, mobile and physical systems, applications and infrastructures where simulated attacks are created.
Users of Cyber ranges vary, from corporates to military to students and therefore a wide scale of usages have been developed through different technical aspects. In this context the report highlights a method to distinguish if a cyber range suits a user’s needs. It is referred to as “Functionalities vs Use Cases” and is displayed in the following table.
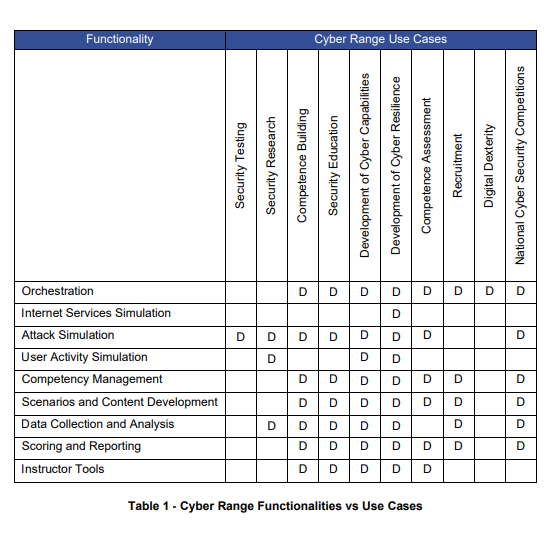
On the above table, choose what you would like to use the cyber range for (Cyber range use cases). Taking the example of security training, you must now check where it matches with the functionality (type of cyber range simulation), in this case the match is only with ‘Attack simulation’. Therefore, if I am searching for security training, I must look for a cyber range with attack simulation.
The report concludes that “cyber ranges are chosen indistinctively with the aim to meet specific use cases only for the realisation that not all cyber ranges are the same, thus resulting in failed expectations.” This is due to the fact that a cyber range is highly customisable, which can lead to a lack of clear understanding of it and its associated technologies.
As recently discussed in some articles on this website, customisation is a key point in cyber security training. Cyber security needs differ greatly from one market user to the next and unless a training course is tailored to them using, the interchangeable functionalities of a cyber range, online learning and moodle modules then they will not receive a return on investment.
CYBERWISER.eu has championed the customisable practical approach to cyber security training and believes it is the best way to democratise cyber security. For more information on CYBERWISER.eu you can read some more information on the right training approach for your organisation here.

 © Copyright 2021 - CYBERWISER.eu has received funding from the European Union’s Horizon 2020 research and innovation programme under the Grant Agreement no. 786668. The content of this website does not represent the opinion of the European Union, and the European Union is not responsible for any use that might be made of such content.
© Copyright 2021 - CYBERWISER.eu has received funding from the European Union’s Horizon 2020 research and innovation programme under the Grant Agreement no. 786668. The content of this website does not represent the opinion of the European Union, and the European Union is not responsible for any use that might be made of such content.